Pentest
Learn how to leverage the HackerOne platform and community to get better, faster results from penetration tests.
-
Read More
Attack Surface Reconnaissance Solution Brief
Attack Surface Reconnaissance (ASR), powered by HackerOne, enhances the efficacy of automation with a team of recon experts who think like adversaries but work for you. They
-
Read More
HackerOne's Pentest Community Solution Brief
Meet HackerOne's pentest community -- the most prestigious segment within HackerOne, valued by the testers themselves and the customers they assist.
-
See our Pentest product video & sign up for a demo here
Get Started -
 Read Article
Read ArticleWhat Do New Cybersecurity Rules Mean For CISOs?
The rule requires public companies to report material cybersecurity incidents and annually report on elements of their cybersecurity risk management and strategy. Companies that are publicly...
-
 Read Article
Read ArticleYou're Doing Pentesting Wrong
Pentesting has been around for decades, but it hasn’t undergone the revolution that other security practices have. Organizations tend to rely on pentesting as a tool to just “check-the-box” for...
-
Read More
6th Annual Hacker Powered Security Report
-
Read More
2022 Buyer’s Guide to Pentesting - How to Choose and Assess the Ideal Pentest Solution for Your Organization’s Needs
Pentests are a foundational requirement for any security program, and come in multiple forms. Our Hacker-Powered pentests can uncover critical findings that traditional pentests often miss. Learn abou
-
 Read Article
Read ArticleInterpret the 2023 GigaOm PTaaS Radar Report with HackerOne
The GigaOm report recognizes and validates the substantial advantages of PTaaS over traditional pentesting, especially for digital-forward organizations. It also provides a technical evaluation of...
-
Explore our catalog of on-demand video content.
View All Videos -
 Read Article
Read ArticleHow Human Security Testing Helps the U.S. Government’s Zero Trust Mandate
One major reason for the progress is a May 2021 Executive Order that pushes federal agencies to speedily embrace the “never trust; always verify” cybersecurity paradigm of Zero Trust. As the 72%...
-
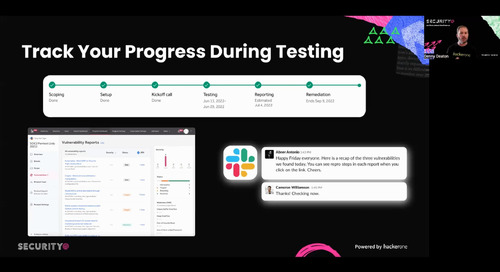 30:09Watch Video
30:09Watch VideoRunning Scalable & Efficient Pentesting Programs with HackerOne
-
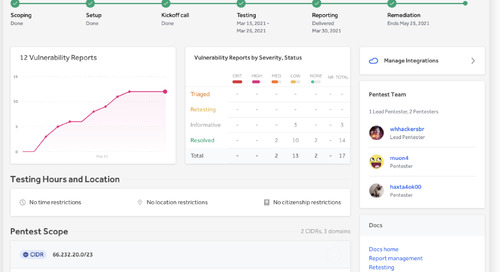 Read Article
Read ArticleUse Hackerone’s Enhanced Pentest as a Service to Streamline Security Testing
New capabilities improve pentesting to increase attack resistance The enhanced features drive robust security testing practices with the ability to launch, test, identify, retest, and fix...
-
Read Article
HackerOne’s Pentest as a Service Enhancements Streamline Secure Testing for Large Enterprises and Digital Innovators
HackerOne’s Pentest as a Service Enhancements Streamline Secure Testing for Large Enterprises and Digital Innovators ejames@hackerone.com Tue, 09/27/2022 - 14:22 Read more about HackerOne’s...
-
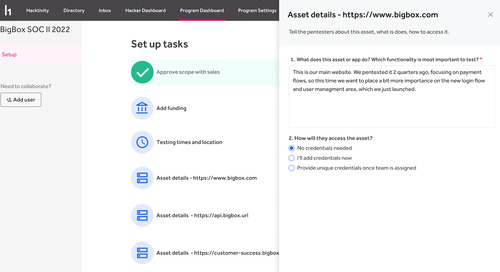 Read Article
Read ArticleHackerOne Announces a New Customer Pentest Setup that's More Efficient and Speeds Time to Launch
This improved experience reduces time to launch, which is vital when your organization is up against an urgent timeline to complete a pentest due to a recent acquisition, a security breach,...
-
 29:04Watch Video
29:04Watch VideoFrom Disclosure to Pentest: Embedding Hackers at Each Step of the Development Lifecycle
-
 28:09Watch Video
28:09Watch VideoLeveraging Assessments + Pentests to Manage Risk
-
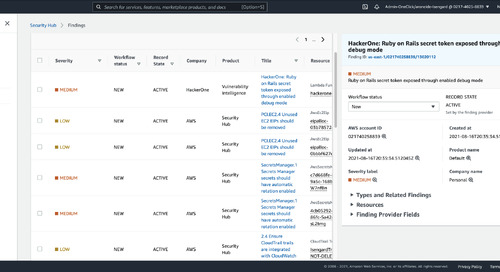 Read Article
Read ArticleHackerOne Announces Hacker-Powered Solutions: Cloud Security Capabilities for AWS Customers
Today HackerOne announced new capabilities for AWS customers looking to improve security in their cloud applications. These include vulnerability pentests specific to AWS environments, an AWS...
-
Read More
Hacker-Powered Security for Safer AWS Cloud Applications
HackerOne and AWS together accelerate the discovery of critical vulnerabilities, streamline AWS security workflows, and strengthen your security teams to mitigate risk.
-
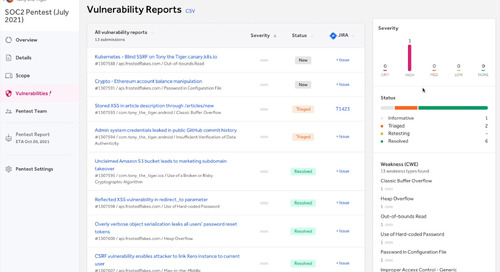 1:28Watch Video
1:28Watch VideoApp Pentest for AWS
-
Read More
The Secret Weapon for Your Modern Pentest: Skilled Hackers
Match testers and by backgrounds and experience to fit your testing requirements for your pentest engagements results.
-
Read More
Rightsline Pentest Case Study
Rightsline is trusted to guard the entertainment industry’s intellectual property. See how they leverage HackerOne to demonstrate their commitment to security and stay proactive against threats.
-
Read More
Top 5 Common Security Assessment Mistakes and How to Avoid Them
Security assessments play an important role in helping organizations determine their cybersecurity readiness and learn about security gaps that should top their priorities list. Learn the top five mos
-
Loading More...







